Token Ring
Token Ring is a network architecture developed by IBM in the 1970s with logical ring topology and token-passing access technique, using a 3-byte frame. > called a witness (in English token) that travels around the ring. Token Ring is defined in the IEEE 802.5 standard. Disused due to the popularization of Ethernet; It is not currently used in network designs.
IEEE 802.5 standard
IEEE 802.5 is a standard by the Institute of Electrical and Electronics Engineers (IEEE), and defines a local area network LAN in ring configuration (Ring), with token passing method as media access control. The speed of its standard is 4 or 16 Mb/s when it is implemented on copper wire cables, there are higher speed implementations both on CDDI copper wires and on FDDI optical fiber which reaches 100 Mbps and 200 km of distance. extension.
The design of a Token Ring network was attributed to E. E. Newhall in 1969. IBM first published its Token Ring topology in March 1982, when IBM submitted the IEEE 802 project papers. IBM announced a Token Ring product in 1984, and in 1985 this became an ANSI/IEEE standard.
It is nearly identical to and fully compatible with IBM's Token Ring network. In fact, the IEEE 802.5 specification was modeled on this Token Ring, and continues to shadow it. In addition, the IBM Token Ring specifies a star, with all end stations attached to a device called a multi-station access unit (MSAU). In contrast, IEEE 802.5 does not specify a topology, although virtually all IEEE 802.5 implementations are based on a star, and also does not specify a media type, whereas IBM Token Ring networks use the size of the information field of routing.
IEEE 802.5 supports two basic frame types: tokens and command and data frames. The witness is a plot that circulates through the ring in its only direction of circulation. When a station wants to transmit and the token passes through it, it takes it. This can only remain in his possession for a certain time (10 ms). They are 3 bytes long and consist of a start delimiter, an access control byte, and an end delimiter. As for the command and data frames, they can vary in size, depending on the size of the information field. Data frames have information for larger protocols, while command frames contain control information.
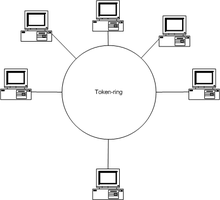
Token Ring Topology
The token ring topology is made up of Multistation Access Units (MAUs) that allow computers to be connected in a star fashion. The distributor is a nodal point connected to all network participants. There is no direct connection between the computers.
Comparison with Ethernet
There are several notable differences between Token Ring and Ethernet:
- Access to Token Ring is more deterministic compared to CSMA/CD-based Ethernet connections
- Ethernet supports direct connections between two network cards by using a crossed cable or by automatic detection, if permitted. While Token Ring does not support such use.
- Token Ring eliminates collision by using a single-use symbol and is committed to early release to relieve downtime. Ethernet relieves collision by multiple access to the carrier's sense and by using a smart switch. Ethernet primitive devices such as concentrators can precipitate collisions due to the repetition of blind traffic.
- The Token Ring network cards are capable of auto detecting speed, routing and are able to drive them through various multi-station access units (MUs) that operate without energy (most MAUs operate this way, requiring only one LED power supply). Ethernet network interface cards can work theoretically on a passive concentrator to a certain degree, but not as a large LAN, plus the issue of collisions is still present.
- Token Ring uses "priority of access" in which certain nodes may have priority over the witness. An uncomputed Ethernet network has no provision for a priority access system, as all nodes have the same behavior during traffic.
- Multiple identical MAC addresses are compatible with Token Ring (a feature used by mainframes S/390). A switched Ethernet network cannot admit duplicate MAC addresses without generating errors.
- Token Ring is more complex than Ethernet, requiring a specialized processor and firmware with MAC/LLC license for each interface. On the contrary, Ethernet includes both the firmware (more simple) and the license with lower cost on the MAC chip. The cost of a Token Ring interface using the Texas Instruments TMS380C16 MAC and PHY is approximately three times that of an Ethernet interface using the Intel 82586 MAC and PHY.
- Initially, both networks used expensive cables, but once Ethernet was standardized for non-armoured braided pairs with 10BASE-T (Cat 3) and 100BASE-TX (Cat 5 (e)), it had a clear advantage and sales increased significantly.
- Even more significant was comparing the overall costs of the system, as the much higher cost of the router ports and the network cards for Token Ring versus Ethernet. The appearance of Ethernet switches was the tip for system evolution.
Main features
- It uses a logical topology in a ring, although through a multiple station access unit (MSAU or MAU), the network can be seen as if it were a star. It has star physical topology and logical topology in ring.
- It uses special wires, although the wiring can also be braided pair.
- The total length of the network cannot exceed 366 meters.
- The distance between a computer and the MAU cannot be greater than 100 meters (by the degradation of the signal after this distance on a braided pair cable).
- Each MAU can connect eight computers.
- These networks reach a maximum transmission rate ranging from 4 to 16 Mb/s.
- Then the high-speed Token Ring (HSTR) increased the speed to 110 Mb/s but most networks do not support it.
MAC in Token Ring
- Scheme format:
| 1 byte | 1 byte | 1 byte | 6 bytes | 6 bytes | ▪ | 4 bytes | 1 byte | 1 byte |
| SD | AC | FC | Say destination | Dir. origin | Information | FCS | ED | FS |
- Format of the witness:
| SD | AC | ED |
- SD/ED (start/ending designator): designator of incio/fin; HH or LL encoding (not valid in differential Manchester).
- AC: Access control.
PPP T M RRR
- PPP: priority.
- T: witness (Yes/No).
- M: Monitoring.
- RRR: priority reserve.
- FC: Frame Control (Type)
- Data (LLC-PDU).
- Control (network maintenance and operation).
- FCS: CRC for mistakes.
- FS: tram stand; it serves for MAC confirmation.
A C rr A C rr
- A: It has passed through destiny.
- C: the recipient has read it.
Operation
- The idea is to keep the witness circulating actively through the ring, so that any station you want to transmit can do so when it passes through it. At this point, the station that receives the witness verifies the priority field of this, if the data you wish to send have a higher or equal priority, then retains the witness during the maximum time of possession less than 10 ms or until you have no more data to send (what happens first) and starts your transmission. As the plots go through the ring, each station verifies whether the Destination address corresponds to its own, if not simply ignores it. Otherwise, the receiving station will copy the plot (notifying this by marking the copying bit in 1) and according to the result of the operation, the bit A will also be turned on; then let the plot continue to circulate through the ring so that upon reaching the transmitter it is withdrawn. Finally, the emitter must inject a new witness into the ring, with priority X (where X will be the priority previously marked in the witness before our station retained it to start the transmission), the objective of this is that the stations with data whose priority is lower do not suffer from starvation and can transmit.
Tips:
- Hosts with P priority data (eight levels).
- Witness Capture: Take advantage of SD from the witness and enter your plot only if the witness's priority is less or equal than that of the data to transmit.
Functionality
Access method
It is known as token passing and it consists in that a single station can transmit at a certain moment and it is precisely the one that possesses the token at that moment, this is the one in charge of assigning the permissions to transmit the data.
Transmission mode
Transmission techniques; Baseband, Manchester directional code, this consists of a bit with a value of 1 indicating the absence of transmission at the beginning of the interval, and a bit with a value of zero indicating the presence of a transition, there is a transition in the middle part of the interval.
Baseband
The signal is transmitted directly in digital form without modulation, so it occupies the bandwidth of the transmission medium, only high or low voltage levels go through the communication line.
Maintenance/monitoring functions
- Supervisory station:
- Monitor the network.
- It regularly sends a control plot type AMP (current active monitor).
- Watch the witness's presence:
- If you don't find it after a while, it puts it back in circulation.
- Watch the length of the witness to be greater or equal to 24 bits (a full witness) adding more if necessary.
- Watch the presence of orphaned plots and remove them:
- Activate the M bit of the plot by passing through it (supervising station), if for the second time the plot is received with the M bit on, it is discarded.
- Watch the presence of mutilated plots and remove them.
Priorities
- Reservation:
- About the RR field of a data plot.
- The person responsible for removing the plot puts the witness in circulation with that priority.
- Reservations can be rewritten by others of higher priority, saved and used afterwards.
Contenido relacionado
Reduced instruction set computing
Ethernet
Applied Science