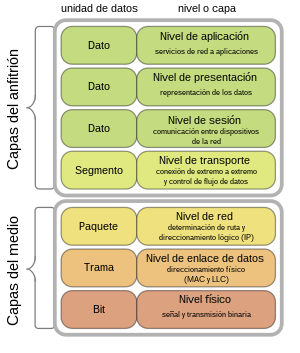
Session layer
The session level or session layer is the fifth level of the OSI model, which provides the mechanisms to control the dialog between applications on end systems. In many cases, session layer services are partially, or even completely, dispensable. However, in some applications its use is unavoidable.
The session layer provides the following services:
- Dialogue Control: This can be simultaneous in both senses (full-duplex) or alternated in both senses (half-duplex).
- Group: The data flow can be marked to define data groups.
- Recovery: The session layer can provide a checkpoint procedure, so that if any type of checkpoint failure occurs, the session entity can relay all data from the last check point and not from the beginning.
All of these capabilities could be incorporated into Layer 7 applications. However, since all of these dialog control tools are widely applicable, it seems logical to organize them in a separate layer, called the session layer.
The session layer arises as a way to organize and synchronize the dialog and control the exchange of data.
The session layer allows users on different machines to establish sessions with each other. A session allows ordinary transport of data, as the transport layer does, but also provides enhanced services that are useful in some applications. A session could be used to connect the user to a remote timesharing system or to transfer a file between two machines.
Objectives
- Allow users of different machines to set up sessions between them
- Allow a user to enter a distance-sharing time system or share remote files.
- Between the administration and completion of the sessions, some key services are carried out for the proper functioning, which are:
- Session control.
- maintain verification points
- Concurrence control (to prevent two processes at the same time)
- Therefore, this layer ensures or maintains the link between two teams and allows to resume tasks in case of any interruption.
- In this layer the traffic of the network is allowed in both directions at the same time or a single direction. If the traffic only goes in one direction, the session layer will help in tracking who has the turn.
- There is synchronization as the layer provides a way to insert verification points into the data flow, with the objective that after each fall, only the data that are after the last verification point are repeated.
- A session looks like a transport connection.
- When a request is made for the session layer to set a session, a transport connection must be established to support the connection
- When the session ends, the transport connection is released.
- Each time an agent answers a call, a session is set with the main team.
- Once an agent answers a call, a session is set with the main team.
- Once the session is processed, the session is terminated
- The important thing at this point is that there is no need to load with the problem of releasing the underlying transport connection.
Session Layer Protocols
- RPC Protocol (called remote procedure): is a protocol that allows a computer program to run code on another remote machine without having to worry about communications between both. The protocol is a major advance on the sockets used so far. The RPCs are widely used within the client-server paradigm, being the client who initiates the process by requesting the server to execute a certain procedure or function, and sending back the latter the result of such operation to the client. Today, the XML is being used as a language to define IDL and HTTP as a network protocol, giving rise to what is known as web services.
- The client makes the call to the remote procedure through a message through the network, it stops as it is a synchronous process, that is, it needs a server response to continue its execution, in this call it includes a STUN (resguard) which is responsible for adjusting parameters and memory addresses in an environment (client) or another (server).
- The server receives the request and unpacks the message to extract the necessary information to perform the task. The stub helps the server be able to convert parameters from one representation to another, to translate customer memory addresses to server.
- The server executes the task.
- The server creates a response message for the client in which it includes the result of the task that it asked to perform
- The client receives and unpacks the server's response message, continues with its normal execution. STUB: The stub is the code piece that allows the server to execute the task assigned to it, is responsible for providing the necessary information for the server to convert the addresses of the parameters that the client sent in valid memory addresses within the server environment. The representation of data between the client and the server could differ, the stub also provides the necessary information to solve this situation. In general, it is the code piece that is responsible for masking all the discrepancy between the client and server, it is necessary that the stubs libraries are installed both on the client and on the server.
- SCP (Secure Copy): The SCP protocol is basically identical to the RCP protocol, but unlike this, the data is encrypted during its transfer, to prevent potential sniffers from extracting useful information from the data packages. However, the protocol itself does not provide authentication and security; it expects the underlying protocol, SSH, to ensure it.
- ASP (APPLE TALK session protocol): It was developed by Apple Computer, offering session setting, maintenance and disassembly, as well as the requested sequence. ASP is an intermediate protocol based on the top of AppleTalk Transactions Protocol (ATP), which is the original and reliable protocol at AppleTalk session level. It provides basic services to request responses to arbitrary orders and to carry out outside the state consultation band. It also allows the server to send asynchronous customer service messages.
Comparison with the TCP/IP model
The TCP/IP model does not deal with the OSI model details of transport or application protocol semantics and therefore does not consider a session layer. OSI session management in relation to typical transport protocols (TCP, SCTP) is contained within the Transport Layer protocols, or is otherwise considered the purview of the Application Layer protocols. The TCP/IP layers are descriptions of operational domains (application, host-to-host, network, link) and not detailed prescriptions of operational procedures or data semantics.
Contenido relacionado
Larry Sanger
Printer
Free Software Foundation