OSI model
The Open Systems Interconnection Model (ISO/IEC 7498-1), known as the OSI model, Open Ssystems Interconnection) is a reference model for network protocols (not a network architecture), created in 1980 by the International Organization for Standardization. It has been published since 1983 by the International Telecommunication Union (ITU) and, since 1984, the International Organization for Standardization (ISO) has also published it as a standard. Its development began in 1977.
It is a standard that aims to interconnect systems of different origin so that they could exchange information without any kind of impediments due to the protocols with which they operated in their own way according to their manufacturer.
The OSI model is made up of 7 layers or levels of abstraction. Each of these levels will have its own functions so that together they are capable of reaching their final objective. Precisely this separation into levels makes possible the intercommunication of different protocols by concentrating specific functions at each level of operation.
The OSI model is not the definition of a topology or a network model itself. Neither does it specify or define the protocols that are used in the communication, since these are implemented independently of this model. What OSI actually does is define the functionality of them to achieve a standard.
History
In the early 1980s, the development of networks caused disorder in many ways. There was tremendous growth in the number and size of networks. As businesses became aware of the benefits of using connection technologies, networks were being added or expanded at almost the same speed that new network technologies were introduced.
In the mid-1980s, these companies began to suffer the consequences of rapid expansion. In the same way that people who do not speak the same language have difficulty communicating, networks using different specifications and implementations could not exchange information. The same problem arose with companies that developed proprietary connection technologies (a technology is called "proprietary" when its implementation (whether software or hardware) is subject to copyright. This assumes that a company controls this technology and companies who want to use it in their systems have to pay royalties for its use). Connection technologies that strictly respected proprietary rules could not communicate with technologies that used different proprietary rules and even with those that used copyleft connection rules.
To address the problem of network incompatibility, ISO investigated connection models such as the Digital Equipment Corporation (DECnet) network, the Systems Network Architecture, SNA) and TCP/IP, in order to find a set of rules generally applicable to all networks. Based on this research, ISO developed a network model to help manufacturers create networks that are compatible with other networks.
OSI Reference Model
It is a standard developed in 1980 by the International Organization for Standardization (ISO), a global federation of organizations representing approximately 160 countries. The core of this standard is the OSI reference model, a regulation made up of seven layers that defines the different phases through which data must pass to travel from one device to another over a communications network.
Numerous protocols were created following the outline of this model. The advent of more flexible protocols where the layers are not so unmarked and the correspondence with the levels was not so clear put this scheme in the background. However it is used in teaching as a way to show how a "stack" of communications protocols can be structured.
The model specifies the protocol to be used at each layer, and is often referred to as a reference model as it is used as a great tool for teaching network communication.
It should always be remembered that it is a model, a theoretical construction, therefore it does not have a direct correlate with the real world. This is a useful standardized regulation due to the existence of many technologies, manufacturers and companies within the world of communications, and being in continuous expansion, a method had to be created so that everyone could understand each other in some way, even when the technologies did not match. Thus, no matter the geographic location or the language used - everyone must adhere to some minimum standards in order to communicate with each other. This is especially important when we talk about the network of networks, that is, the Internet.
The OSI Reference Model is the descriptive network model, which was created by the International Organization for Standardization in the year 1980. It recognized that there was a need to create a network model that could help network designers implement networks. that they could communicate and work together and therefore developed the OSI Reference Model. The core of this standard is the OSI reference model, a regulation made up of seven layers that defines the different phases through which data must pass to travel from one device to another over a communications network. The model specifies the protocol that must be used in each layer, and is often referred to as a reference model since it is used as a great tool for teaching network communication.
There are different protocols according to how the communication is expected to be. This suite of protocols is called TCP/IP. TCP/IP has become the de-facto standard for corporate networking. TCP/IP networks are highly scalable, so it can be used for both small and large networks.
TCP/IP is a suite of routed protocols that can run on many different software platforms and is supported by almost all network operating systems as the default network protocol. Member protocols of the TCP/IP stack. FTP, SMTP, UDP, IP, ARP. TCP runs on several layers of the OSI Internet Protocol model. It is a connectionless protocol used by both the source and destination for data communication over a packet-switched network. Data on an IP-based network is sent in blocks known as packets or datagrams.
| Number | Name | Responsibility | Description |
|---|---|---|---|
| Layer 7 | Implementation | Head of network services for applications | It differs from other layers because it does not provide services to any other OSI layer, but only to applications that are outside the OSI model. The application layer establishes the availability of potential communication partners, synchronizes and establishes agreements on error recovery procedures and data integrity control. This ensures that the information sent by the application layer of a system can be read by the application layer of another. If necessary, the presentation layer translates between several data formats using a common format. |
| Layer 6 | Presentation | Transforms data format and provides a standard interface for the application layer | Its objective is to take care of the representation of the information, so that although different teams may have different internal representations of characters numbers, sound or images, the data arrive in a recognizable way. This layer is the first to work more on the content of the communication than on how it is established. It addresses aspects such as semantics and syntax of transmitted data, as different computers may have different ways of handling them. Therefore, we can summarize by defining this layer as the one responsible for managing abstract data structures and performing the data representation conversions necessary for the correct interpretation of them. This layer also allows data to be encrypted and compressed. |
| Layer 5 | Session | Establish, manage and finalize connections between local and remote applications | As its name implies, the session layer establishes, manages and finalizes the sessions between two hosts that are communicating. The session layer provides its services to the presentation layer. It also synchronizes the dialogue between the filing layers of the two hosts and manages their data exchange.
In addition to regulating the session, the session layer offers provisions for efficient data transfer, service class and a record of exceptions regarding the problems of the session, presentation and application layer. But this protocol must be transported between machines through other protocols. With SAP, servers allow routers to create and maintain a database with the updated information of the interred servers. The transport layer segments the data originated in the host issuer and rethinks them in a data stream within the host system. |
| Layer 4 | Transport | Provides reliable transport and flow control across the network | The limit between the transport layer and the session layer can be imagined as the limit between application protocols and data flow protocols. While application, presentation and session layers are related to application issues, the four lower layers are responsible for data transport. TCP creates connections through which it can send data flows. The protocol guarantees that the data will be delivered to your destination without error and in the same order in which they were transmitted. |
| Layer 3 | Red | Responsible for the logical direction and domain of routing | Its mission is to get data from origin to destination even if they do not have direct connection. IPX/SPX It is a network protocol family developed by novell and used by its netware operating system. The IPX is a fast communication-oriented data chart protocol that is responsible for transmitting data through the network, including in each package the destination address. The data link layer provides reliable data transit through a physical link. |
| Layer 2 | Data Link | Provides physical guidance and media access procedures | In doing so, the data link layer deals with physical direction, network topology, network access, error notification, orderly delivery of plots and flow control. Ethernet defines the wiring and signaling characteristics of the physical level and data shear formats of the data link level. FDDI Provides 100 standard optical Mbits/s for data transmission in a local area network. |
| Capa 1 | Physics | Defines all electrical and physical specifications of devices | The physical layer defines electrical, mechanical, procedural and functional specifications to activate, maintain and deactivate the physical link between final systems.
Features such as voltage levels, voltage change timer, physical data speed, maximum transmission distances, physical connectors and other similar attributes are defined by the physical layer specifications. Bluetooth is an industrial specification for Personal Area Wireless Networks that enables voice and data transmission between different devices. ADSL It consists of an analogue transmission of digital data supported in the symmetrical copper pair that carries the conventional phone line. USB It is an industrial standard developed in the 1990s that defines the cables, connectors and protocols used on a bus to connect and provide power supply between computers, peripherals and electronic devices. It consists of an analogue transmission of digital data supported in the symmetrical copper pair that carries the conventional phone line. |
Layered architecture
The X.22 recommendation describes a model of seven layers or levels numbered from 1 to 7 with 1 being the lowest.
| Layer | Protocol Data Unit (PDU) | Function | ||
|---|---|---|---|---|
| Host
layers | 7 | Implementation | Data | High-level APIs, such as sharing resources and remote access to files |
| 6 | Presentation | Data translation between a network service and an application, including character encoding, data compression and data encryption and decryption | ||
| 5 | Session | Management of communication sessions, for example the continued exchange of information in the form of multiple transmissions on both sides between two nodes | ||
| 4 | Transport | Segment | Transmission of reliable data segments between network points, including segmentation, acknowledgement and multiplexation | |
| Media
layers | 3 | Red | Package, Datagram | Structure and management of a multinode network. Includes direction, route and traffic control |
| 2 | Data link | Trauma | Reliable data transmission between two nodes connected by a physical layer | |
| 1 | Physics | Bit, Baudios | Transmission and receipt of unprocessed bit flows by a physical medium | |
| Physical layer | 0* | Media | dBm | Physical means of transmission, can be optical (photonic), electrical (normally copper) or wireless. It is especially relevant in phone transmission networks such as DWDM. |
Middle Layer - Layer 0* (Layer Zero)
This layer is a topic that generates a lot of discussion, since it is not officially recognized in the OSI model. However, in practice the term is commonly used to refer to the transmission medium, whether wired or wireless. It has special relevance in the world of Carriers as it is used to explain everything related to photonic networks and multi-wavelength transmission systems (DWDM). On the other hand, in the world of Datacenters, layer 0 is referred to as everything related to infrastructure such as cabling between racks and rooms, as well as everything related to intra-rack cabling.
Physical Layer - Layer 1
It is the lowest layer of the OSI model. It is the one that is in charge of the network topology and the global connections of the computer to the network, it refers both to the physical environment and to the way in which information and networks are transmitted.
Its main functions can be summarized as:
- Define the medium or physical means by which the communication will travel: cable of braided pairs (or not, as in RS232/EIA232), coaxial cable, wave guides, air, optical fiber.
- Define the electrical characteristics (voltage levels) and materials (components and mechanical connectors) to be used in the transmission of data by physical means.
- Define the functional features of the interface (establishment, maintenance and release of the physical link).
- Transmit the bit flow through the middle.
- Handle the electrical signals of the transmission medium, poles in a plug, etc.
- Guarantee the connection (although not the reliability of the connection).
Data Link Layer - Layer 2
This layer deals with physical addressing, media access, error detection, orderly distribution of frames, and flow control.
It is one of the most important aspects to review when connecting two computers, since it is between layer 1 and 3 as an essential part for the creation of its basic protocols (MAC, IP), to regulate the way of the connection between computers, determining the passage of frames (unit of measurement of the information in this layer, which is nothing more than the segmentation of the data transferring them by means of packets), verifying their integrity, and correcting errors.
For this reason, it is important to maintain an excellent adaptation to the physical medium (the most used are UTP, twisted pair or 8-wire cable), with the network medium that redirects the connections through a router.
Given these situations, it should be noted that the device used by the link layer is the Switch that is in charge of receiving the data from the router and sending each of these to their respective recipients (server -> client computer or some other device that receives information such as mobile phones, tablets and different devices with access to the network, etc.), given this situation, it is determined as the means that is in charge of error correction, frame handling, data protocolization (protocols are called the "rules of courtesy" or conventions that any layer of the OSI model must follow).
Network Layer - Layer 3
It is responsible for identifying existing routing between one or more networks. The data units are called packets, and can be classified into routable protocols and routing protocols.
- Routables: travel with packages (IP, IPX, APPLETALK)
- Routing: allow to select routes (RIP, IGRP, EIGRP, OSPF, BGP)
The goal of the network layer is to get data from the source to the destination, even when the two are not directly connected but use intermediate devices. The devices that facilitate this task are called routers, although it is more common to find them under the English name routers. The routers work in this layer, although they can act as a layer 2 switch in certain cases, depending on the function assigned to it. The firewalls mainly act on this layer, to rule out addresses of certain machines or limit access to certain of them.
At this level, the logical addressing and the determination of the route of the data to its final receiver are carried out.
Transport Layer - Layer 4
Layer in charge of transporting the error-free data (which is inside the packet) from the source machine to the destination machine, regardless of the type of physical network being used.
The layer 4 PDU (information unit) is called a segment or datagram, depending on whether it corresponds to TCP or UDP, the first connection-oriented (transmission verified, eventually retransmitted) and the other connectionless (some data may be lost). data along the way). They work, therefore, with logical ports and together with the network layer they shape what is known as Sockets IP:Port (example: 191.16.200.54:80).
Session Layer - Layer 5
This layer is responsible for maintaining and controlling the link established between two computers that are transmitting data of any kind. Therefore, the service provided by this layer is the ability to ensure that, given a session established between two machines, it can be carried out for the defined operations from start to finish, resuming them in case of interruption. In many cases, session layer services are partially or totally dispensable.
Presentation Layer - Layer 6
The goal is to take care of the representation of the information, so that even though different computers may have different internal representations of characters, the data arrives in a recognizable way.
This layer is the first to work more on the content of the communication than on how it is established. It deals with aspects such as the semantics and syntax of the transmitted data, since different computers may have different ways of handling them. For example, the same website can adapt the presentation of its data depending on whether it is accessed from a conventional computer, a tablet, or a smartphone.
This layer also allows data to be encrypted and compressed. Therefore, it could be said that this layer acts as a translator.
Application Layer - Layer 7
It offers applications the possibility of accessing the services of the other layers and defines the protocols that applications use to exchange data, such as email (Post Office Protocol and SMTP), database managers and file servers. (FTP). There are as many protocols as there are different applications and since new applications are continually being developed the number of protocols is constantly growing.
It should be noted that the user normally does not interact directly with the application layer. It usually interacts with programs that in turn interact with the application layer but hide the underlying complexity.
Mnemonic Rule
In order to facilitate learning and memorizing the names of the layers that make up the model; A simple rule is to memorize them as a mnemonic acronym: FERTSPA, which in English would sound like First Spa (first spa in Spanish) which is defined as follows:
- Física
- Enlace
- Red
- Transport
- Sesion
- Presentment
- Aplication
There is a mnemonic phrase that makes it easier for Spanish-speakers to memorize: Some Ppeople Shold that All Rnetworks are EFeffective. It corresponds with its descending order:
- Aplication
- Presentment
- Sesion
- Transport:
- Red
- Enlace
- Física
Note: Its authorship is attributed to Tomás Murillo, professor of Telematic Systems and other subjects at the I.E.S. Salesians Zaragoza "Ntra. Mrs. del Pilar, Zaragoza.
Data units
The exchange of information between two OSI layers consists of each layer in the source system adding control information to the data, and each layer in the destination system parsing and removing control information from the data as follows:
If one computer (A) wants to send data to another (B), the data must first be packaged through a process called encapsulation, that is, as the data moves through the layers of the model OSI, receive headers, trailing information, and other types of information.
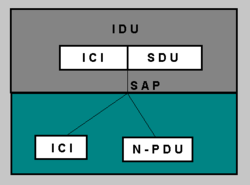
N-PDU
The protocol data unit (N-PDU) is the information exchanged between peer entities, that is, two entities belonging to the same layer but in two different systems, using a N-1. Is composed of:
- N-SDU (Service Data Unit): the data required by the entities
Nto perform functions of the service requested by the entityN+1. - N-PCI (Protocol Control Information): information exchanged between entities
Nusing a connectionN-1to coordinate their joint operation.
N-IDU
The Interface Data Unit (N-IDU): is the information transferred between two adjacent levels, that is, two contiguous layers. Is composed of:
- N-ICI (Information of Interface Control): information exchanged between an entity
N+1and an entityNto coordinate their joint operation. - Interface Data-(N): information transferred between an entity-
(N+1)and an entity-(N)and that usually matches the(N+1)-PDU.
Transmission of data
The application layer receives the message from the user and adds a header to it, thus constituting the application layer PDU. The PDU is transferred to the application layer of the destination mode, which removes the header and delivers the message to the user.
This whole process has been necessary for this:
- The PDU must now be delivered to the presentation layer to add the corresponding ICI header and thus transform it into an IDU, which is transmitted to that layer.
- The presentation layer receives the IDU, removes the header and extracts the information, that is, the SDU, to this adds its own header (PCI) thus forming the PDU of the presentation layer.
- This PDU is transferred in turn to the session layer through the same process, thus repeating itself for all layers.
- Upon reaching the physical level, the data received by the physical layer of the receiver are sent.
- Each layer of the receiver deals with extracting the header, which had previously added its homologous layer, interpreting it and delivering the PDU to the top layer.
- Finally, it will reach the application layer, which will deliver the message to the user.
Data format
Other data receives a series of names and specific formats depending on the layer in which it is found, due to the adhesion of a series of headers and final information as described above. The information formats are those shown in the graph:
- APDU
- (layer 7) data unit in the application layer.
- PPDU
- (layer 6) data unit in the presentation layer.
- SPDU
- (box 5) data unit in the session layer.
- TPDU
- (capa 4) data unit in the Transport Segment or Datagram.
- Package
- (layer 3) data unit in the network layer.
- Trauma
- (layer 2) data unit in the data link layer.
- Bit
- (layer 1) data unit in the physical layer.
Operations on the data
In certain situations it is necessary to carry out a series of operations on the PDUs and thus facilitate their transport, because they are too large or because they are too small and we would be wasting the capacity of the link.
Lock and Unlock
Blocking maps multiple (p)-SDUs into one (p)-PDU.
Unblocking identifies multiple (p)-SDUs that are contained in one (p)-PDU.
Concatenation and separation
Concatenation is a (N)-function that performs the (N)-level and maps multiple (N)-PDUs in a single (N-1)-SDU.
Separation identifies multiple (N)-PDUs that are contained in a single (N-1)-SDU.
Security
Networks enable communication between computers and other "smart" like tablets and phones, but they are also the primary means by which these devices are infected with viruses or attacked to steal information. Secure network environments are a growing need. The OSI model makes it easy to classify the different known attacks and the actions to avoid them or at least mitigate their consequences.
Contenido relacionado
Gary Kildall
BitTorrent
ECS